More Than Just a Free Newsletter
Become a Tame Your Practice member for FREE and receive our newsletter, special offers, and exclusive members-only content.
TYP Articles
Important content and news for mental health professionals.
This archive contains all of the publicly published articles on the Tame Your Practice site. If you’re looking for my EHR reviews, you can find them here. For exclusive content, only available to Members (it’s free!) head here.
Note: There are a lot of articles here! It may take a few seconds to load.

MHP Office – Review
MHP Office originally was on a fast track for growth. While maintaining one of its strongest selling points, the “Checkout Wizard”, it had added further standout features that make it a viable application for many practitioners.
Minimizing the Risks of Discussing Clients Online
This comes with some caveats, however. The most important one, in my opinion, is the need to protect our clients' (and prospective clients') privacy by being mindful about how we address case consultation and referrals online.

TheraSoft – Review
Therasoft Online put some significant improvements and new features in place the last time I evaluated it. Particularly noticable is the much more friendly user interface that resulted from a facelift and overall design overhaul.

Therapist Checklist for Going Paperless
I often help mental health clinicians create and follow-through with a plan to go paperless in their private practice. Following is a brief checklist of what that often entails:

SimplePractice – Review
Since its launch in 2013, SimplePractice quickly became a leading application for solo providers and now they have expanded their feature set to include clinician groups.

Your Software and Devices Are Not HIPAA Compliant
With growing frequency, vendors market their software, devices, and services as "HIPAA Compliant". This feeds into the mistaken belief that such beasts exist. It's somewhat understandable.

Carepaths EHR – Review
Carepath's eRecord application packs an impressive array of features. They have all the major feature categories covered and have some unique offerings like a complete suite of note and assessment templates.

Who Owns The Data In Your EHR?
We've probably all done it. Signed a contract or checked an “I agree to the terms and conditions” box on a web site without a thorough reading of the terms. I'll readily admit that I've done it dozens of times. There are certain instances, however, when it's imperative that we read through such agreements.

Jane – Review
Jane, based in Canada, has been around for several years. Only more recently, however, has it become a viable practice management system marketed to behavioral health practitioners, especially those in the United States.

Desktop, Laptop, Tablet, Hybrid?
In my private practice consulting work, I'm often asked by mental health professionals which type of computer they should get. It wasn't that long ago that the choices were simple.

TrueCrypt No More?
In an odd development within the last 24 hours, the TrueCrypt site as well as the download site at SourceForge have delivered an announcement that TrueCrypt is no longer being developed and will not be safe to use.

EHR Your Way – Review
EHR Your Way's core selling point is the ability to take your current forms (progress notes, treatment plans, forms you're required to complete as part of a contract, etc.) and integrate them into a robust practice management system.

Does Your EHR Vendor Sell Your Patients’ Data?
Many of us are concerned, even wary, about what health insurance companies do with the medical data they collect about us and our clients. What's perhaps even more concerning is the prevalence of such data being used, traded, and sold by other entities, including some EHR (Electronic Health Record) vendors.

Going Paperless – Verify and Backup Remotely
In carrying out these tasks, it's important to be mindful since there are legal and ethics implications. To ensure proper conversion, recall these two key terms: Verify and Backup Remotely.

TherapyNotes – Review
TherapyNotes is a solid contender for those desiring a user-friendly, efficient system and willing to wait for a full-featured Client Portal.
EHR – Practice Management System Features – Clients
While it would be nice if EHR / Practice Management Software would produce clients for us, this feature is about tracking client data. At a bare minimum, practitioners have a need to track names and contact information for clients

EHR – Practice Management System Features – Notes
Proress Notes are an integral part of the work of mental health and wellness professionals. Keeping good clinical notes allows a provider to recall information more readily, focus on targeted goals, and track progress.

EHR – Practice Management System Features – Scheduling
A private practice doesn't exist without client appointments. Unless the practitioner or office manager is gifted with perfect memory, a tool for keeping track of those appointments is necessary.
ICD-10 for Behavioral Health – Oct. 1, 2014 Deadline (Delayed)
No one can say that you don't have to be on your toes to keep up with changes in the field of mental health. 2013's big changes included new CPT codes and the DSM-V. This year's will include ICD-10 and the latest stage of implementation of the Affordable Care Act, also known as Obamacare.

PsychAdvantage – Review
Compulink Psychadvantage has been around a while and, like Valant, has recently begun offering restructured pricing in an attempt to address the mental health market.

HIPAA Final Rule Templates and Requirements
The Final Rule brought many changes to the game. In order to be fully compliant, there are some specific things Covered Entities need to have in place.
TYP Privacy Policy
This policy explains how Rob Reinhardt, LPC, PA (owner/operator of the Tame Your Practice web site and used interchangably below) may collect, use and aggregate personal information about you on https://www.tameyourpractice.com. Rob Reinhardt, LPC, PA respects your personal privacy and is committed to protecting it.

CounSol – Review
CounSol is a standout choice for solo clinicians who desire the ability to customize. In 2015 they introduced electronic claims filing and now also feature integrated ERAs.

Therapy Charts – Review
I was impressed by the demo I was given of TherapyCharts. The GUI/UX is well done and it's obvious a lot of thought was put into work flow.

THERAPlatform -Review
THERAPlatform is a service where the primary feature has always been telehealth and the practice management system has grown around it.

Business 101 – Return On Investment
I don't believe it is news to any of us that most mental health professionals don't have a strong business background. This is not surprising considering the topic is rarely even brushed against in our graduate level coursework.

Health Information Exchanges (HIE) and How They May Affect Your Practice
Health Information Exchanges (HIE) are an initiative related to the Affordable Care Act and the HITECH Act. Their purpose is to ease the communication between the EHR/systems of various providers of health care, because the EHRs themselves are behind in doing so (i.e. interoperability).

Therabill – Review
Since that time, WebPT has acquired TheraBill. It's important to note that TheraBill started out as an OT/ST/PT software that then extended it's market to mental health professionals.

Delphi PBS – Review
Delphi is a true dinosaur in the cloud-based practice management system market, pre-dating most of the other offerings. Unlike many of the “traditional” practice management systems that have struggled to keep pace with new rush toward cloud-computing, Delphi has adapted and continued to keep pace with changes in the industry.

Affordable Electronic Records (EMR, EHR) for Mental Health Professionals
One of the top concerns I hear expressed about keeping electronic records in a cloud-based system are the ongoing monthly costs.

PIMSY – Review
PIMSY is rare in that it is a Meaningful Use Certified EHR that was developed specifically for mental health professionals from the start.

CentralReach – Review
CentralReach starts off with a wonderful premise and shows a lot of promise. A newcomer to the market (launched in late 2012), CentralReach endeavors to not only provide a Meaningful-Use Certified EHR for mental health professionals, but also a tool through which users and other professionals can collaborate.

Best Practices for Data Security
One need only read the harrowing tale of the destruction of Mat Honan’s digital life to understand the importance of securing our data. Passwords aren't enough.

All Call Technologies – Virtual Receptionist
We use All Call Technologies for our private practice and can personally vouch, not only for the quality of the product, but the great customer service and attention to detail paid by the staff

EHR – Practice Management Systems In The Cloud
In this series, I discuss and evaluate cloud-based EHR/practice management systems. These are online software solutions that allow you to manage various facets of your practice electronically, typically through a web browser.

Finding the Balance With Privacy and Quality Care
Can we, as mental wellness practitioners strike a balance between respecting client privacy and providing convenient quality care?

Passing On Credit Card Fees – Do Or Don’t?
Imagine going to your favorite restaurant or store one day and seeing a new two to three percent surcharge on your bill? When you ask, they inform you of a new policy that calls for passing credit card merchant fees on to the customer. How would you feel?

Choosing A Crowdfunding Platform – A Traveling Blog Series
Mental health professionals (and others!) often have great ideas for products that never make it to market. Often the primary barrier is that of initial funding for the project.
EHR – Practice Management System Features – Client Portal
How much time and money would your practice save if it no longer had to worry about reminding Clients about appointments? What if you no longer had to print Intake forms and assessments?

Is Your Practice Prepared For Any Contingency? A Professional Will Is Not Enough
There has been a lot of emphasis in recent years on creation of a professional will, a document that clarifies who has responsibility for client records and finances, should a therapist die. While a professional will is a great start, it is not enough.

Therapy Appointment – Review
TherapyAppointment 2.0 has arrived (2019), and it looks great! TherapyAppointment was one of the first applications in this market that serves solo and group behavioral health private practices.

TheraNest – Review
TheraNest continues to develop and add new features at a rapid pace. Their newest is the integration of secure video, allowing clinicians to schedule and hold telehealth sessions with clients.

Providing Telehealth Services – Opportunities and Cautions
Evidence is mounting that, under the right circumstances, telehealth can be as effective as in-person delivery of services. Consequently, interest in this mode of service delivery has been increasing swiftly and exponentially.

TherapyZen – Review
Considering it just became publicly available in 2016, TherapyZen is already off to a solid start. From the helpful set up wizard to the clean, user-friendly interface, there's a lot to like.

ICANotes – Review
ICANotes has made some improvements since my last update. Most notably, they've shined and polished their scheduling system. In my opinion, it's the most aesthetically pleasing part of the application and now has robust availability search functionality.

WriteUpp – Review
WriteUpp doesn't set out to be everything to everyone. In fact, they are counting on a target market for those who want the most basic of practice management solutions. They're off to a good start in that respect, with a nice clean, uncomplicated interface.

EHR – Practice Management Systems and HIPAA
A primary concern for HIPAA Covered Entities when evaluating cloud based applications is whether they are HIPAA compliant. The short version is, if you file insurance claims electronically, you are likely a HIPAA Covered Entity.

Tame Your Practice Free Membership
Tame Your Practice membership is free and provides therapists access to exclusive content, discounts, and deals from partners!
TYP Terms of Service
PLEASE READ THESE TERMS AND CONDITIONS OF USE CAREFULLY BEFORE USING THIS SITE

Medicare Doc Fix Applied and New CPT Codes In Effect
With the House voting yesterday to approve the latest "avoid the fiscal cliff" bill and President Obama promising to sign it, the Medicare "doc fix" will once again occur.

QuicDoc Office – Review
DocuTrac, Inc. has been around for quite some time, starting as a traditional software program focused on documentation. They eventually acquired Office Therapy, primarily to serve as the financial piece of the practice management system.

EHR / Practice Management System Features – Billing
I feel pretty safe in stating that most mental health and wellness professionals are not in this line of work primarily for the money. Still, most of us in private practice are hoping to make a living or at least supplement our income.

Office Ally – Review
Many of the features one might want in a Practice Management System are present in the free version of the OfficeAlly product (Practice Mate). The pieces that aren't there can be found in Patient Ally (Client Portal) and EHR 24/7 (More refined EHR features).

Cloud Practice Management System EHR/EMR – Reviews
Technology expert, Licensed Professional Counselor, and CEO of Tame Your Practice, Rob Reinhardt provides his insightful reviews of EHR - Practice Management Systems intended for therapists in private practice.

HIPAA Final Rule and the Conduit Exception
Probably the hottest topic is the expansion of the definition of Business Associate and the clarification of the Conduit Exception.

ClinicTracker – Review
ClinicTracker is an application to investigate for larger practices (at least ten users) needing a robust feature set, customization options, and/or a Meaningful Use certified EHR. Small therapy-centric private practices may find ClinicTracker to be overwhelming and cumbersome.
ICD-10 Checklist – Prepare for October 1st!
What changed with ICD-10? Read this for a reminder and for a handy checklist for weathering simliar insurance/billing/coding updates.

Empathic – Review
When you combine these missing and underdeveloped features with the price point, Empathic drops into the realm of “Not Likely Contender” for most practices.

EHR – Practice Management System Features – HIPAA Redux & TOS
One of the most important things I've learned during my evaluation of Cloud-Based EHR / Practice Management Systems is that not all HIPAA Business Associate Agreements (BAA) are equal. This was brought into focus for me when I had an attorney, specializing in HIPAA, review the BAA of one of the vendors.

eTherapi Listing Therapists Without Permission?
It was brought to my attention through one of Tamara Suttle's wonderful Private Practice From the Inside Out channels, that eTherapi appears to be listing thousands of therapists without their permission.

Valley Hope iAC/ESS – Brief
This system was developed for a residential chemical dependency treatment program and they are now hoping to branch out to offer it to other providers.

Procentive – Review
Procentive is another in the class of Meaningful Use Certified EHRs that has been working to broaden its marketing appeal. All but solo, part-time practitioners who want integrated insurance filing are likely to find a pricing and features plan that might work for them with Procentive.

Technology, and Board Games, and Creativity!
It was March and I was at the American Counseling Association Conference in Orlando. My primary goals for the conference were to rock the two presentations I was involved in and to network, network, network.

EHR Good, Cloning Bad
One of the strongest selling points of an EMR/EHR or Practice Management System, is the potential for huge time savings. When well programmed and structured, most tasks can be completed in these systems through pull down menus and mouse clicks.

What Health Care Professionals Can Learn From Edward Snowden
Whether you see Edward Snowden as a patriotic whistle blower or a traitor to his country, he has some valuable insights into technology and privacy.

Think You’re Too Small For A HIPAA Fine?
The ensuing investigation resulted in HONI agreeing to pay a $50,000 settlement to the HHS Office for Civil Rights (OCR). It's important to note that the fine wasn't a direct result of the breach.

MyClientsPlus / Jituzu – Review
At first glance, the combination of MyClientsPlus and Jituzu seems enticing. They have all the major feature groups covered and Jituzu even offers integrated credit card processing. The gloss quickly fades however,

STEPNotes – Review
STEPNotes was developed by Dr. Rhonda Sutton when she realized that most counselor education programs didn't adequately address the completion of good progress notes.

Pieces of the Paperless Office Puzzle
While many mental health and wellness professionals are interested in an integrated practice management system, there are those that wish to keep their systems and information separate. For many this is driven by relationships.

HIPAA Compliant Email For Therapists
As a mental health professional, you've probably been hearing a lot about how you should encrypt your email communications with clients. This is true, with some caveats.

EMR vs. EHR Redux
It's important to note that a clearer distinction between Electronic Medical Record (EMR) and Electronic Health Record (EHR) has taken hold here in the United States.

TherapyMate – Review
TherapyMate is relative newcomer to the scene, and has made some significant improvements since my original review. It sports a clean, well-organized interface and pricing based on the number of active clients.
TYP Comment Policy
Tame Your Practice's policy on the posting of blog comments.

Cloud Practice Management System EHR / EMR – Table of Contents
Table of Contents for an article series explaining EHR, EMR, Practice Management systems and leading up to reviews and selection.

Why Is Yodle Health Calling Me?
It appears that Yodle is heavily targeting mental health practitioners for new business. In addition to receiving the cold calls myself, I've received multiple reports from others who have received them as well.

Recommended Technology, Tools, and Resources for Therapists and Counselors
Recommendations for technology, web sites, secure email, phone, credit card processing, therapy tools/interventions, podcasts, and much more!

The Impact of the Affordable Care Act on Mental Health Private Practices
Ever since the Affordable Care Act (aka ACA or Obamacare) was passed in 2010, people have been speculating as to how it would impact mental health providers in private practice.

Understanding Crowdfunding Lingo – A Traveling Blog Series
Choosing which crowdfunding platform to use for a project is one of the most important decisions to make and one that should be settled on early in the process.

How Easy Can Encrypted Email Be?
If you are a user of Gmail, you may have noticed something new recently. A small red padlock has been mysteriously appearing on some of the emails you are receiving or composing.

BestNotes – Review
BestNotes started out as a solution for residential treatment homes and retains a significant market share there. They've eventually recognized the usefulness of their tool in other environments and have expanded their marketing to include those providing outpatient therapy.

Enhancing Security Online – Multi-factor or Two-Factor (2FA) Authentication
In addition to using strong-passwords, and a password manager (I use LastPass), I strongly encourage everyone to use Multi-Factor Authentication (now, more commonly referred to as Two-Factor Authentication or 2FA) whenever possible.

How Do Domain Names Work?
Therapists aren't alone in being confused about domain names. Despite the Internet being commonplace for over twenty years now, the inner workings of Domain Name Service remain a mystery to many.

Crowdfunding Your Product – A Traveling Blog Series
Many of us have experienced it. We've hit upon a wonderful idea for a product. Something we'd like to have; something we know our friends and colleagues would value. We've even figured out what it would look like and how to use it.

ClinicSource – Review
Still, ClinicSource's pricing suggests that it's a notch above the other applications in its market. In many areas of the application it is evident that there is more attention to detail and some features that other applications lack.
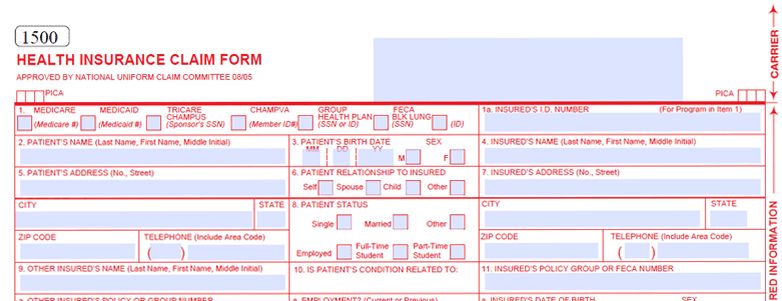
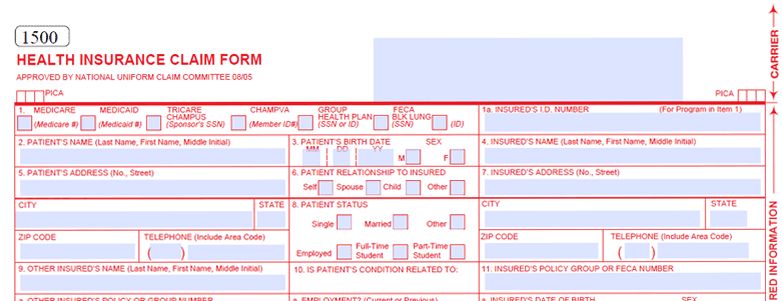
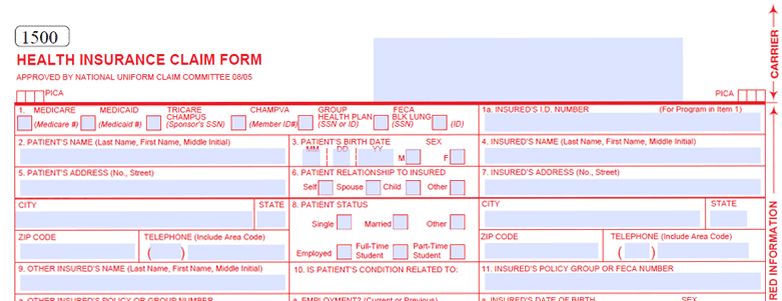
EHR Practice Management System Features – Electronic Claim Filing
If you've been following this series, you've probably noticed I bring up time and money a lot. Specifically I point to how the various features of Cloud-Based EHR / Practice Management Systems have the potential to save practices a significant amount of both time and money.

PSYBooks – Review
One of the most impressive aspects of PSYBooks is that it has come out of the gates with ERA functionality. Most applications have added that long after launching since it can be one of the more complex features to implement.

The Fiscal Cliff, SGR, and You
The SGR referenced in this article was ended by the Medicare Access and CHIP Reauthorization Act signed into law by President Barack Obama in 2015. This article remains published for reference.

How To Recognize and Avoid Phishing Attacks
How do you avoid a phishing attack? No, I'm not talking about rampaging schools of piranha, nor the venerable, ever touring rock band. I don't even mean that amazing ice cream flavor that references the aforementioned rock band.

Meaningful Use and Mental Health Professionals
Meaningful Use, in relation to EHRs, is an incentive program run by the Centers for Medicare and Medicaid Services along with regional supporting offices. The goal of the program is to encourage the adoption of EHRs by eligible professionals (EPs), eligible hospitals and critical access hospitals (CAHs)

Are You Responsible For Fraudulent Credit Card Charges?
ICD-10 isn't the only change that happened in October of 2015. Credit cards also implemented new technology in efforts to become more secure.

EHR – Practice Management System Features – Miscellaneous
In the previous articles, I have covered the major features and concerns when evaluating a Cloud-Based Practice Management System. There are quite a few more things to consider that are less universal and/or don't require full article unto themselves.

Practice Fusion – Review
At the beginning of March, 2018, Practice Fusion announced that they will no longer be offering free accounts as of June 1, 2018. New users must sign up for a paid account and current users must sign up for a subscription by May 31, or be given limited access.

Do I Need to File a BOIR?
Who Needs to File a BOIR? Has it been delayed? What is a BOIR?

Cloud Practice Management System – EHR? EMR?
Some readers of this series on Cloud-Based Practice Management Systems have asked why I've not been using the current buzz terms like EHR and EMR. I thought I'd take a brief opportunity to explain.

Vālant – Review
Long-time readers may remember that I initially ruled Valant out as product for solo and small group practices to consider because of it's pricing.

Potential Privacy and HIPAA Compliance Concerns with Square
I have been using Square (also known as SquareUp) since 2012 and have been very pleased with the service. I've recommended it to countless mental health clinicians looking for an easy, affordable way to accept credit cards. For those who may not have seen it yet,

BreezyNotes – Review
Like so many of these applications, BreezyNotes started out as an application developed by a mental health professional who couldn't find an application that met their needs. In 2015, that application was put out for general public use and is adding features on a regular basis.
Web Sites For Therapists – Where To Go?
I regularly visit many online forums for therapists and one of the questions I hear asked most frequently is, “What's the best way to create my web site?”

TherapyPartner – Review
TherapyPartner has been a player in the realm of cloud-based mental health practice management services for many years. Their original focus was to provide automated credit card billing and statement generation and their primary target market has been professionals in a fee for service practice.


